Hypertext transfer protocol


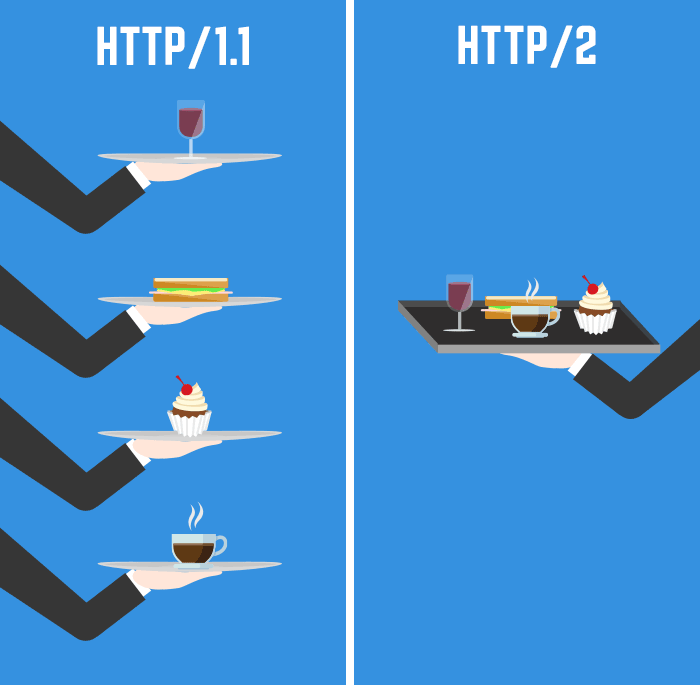
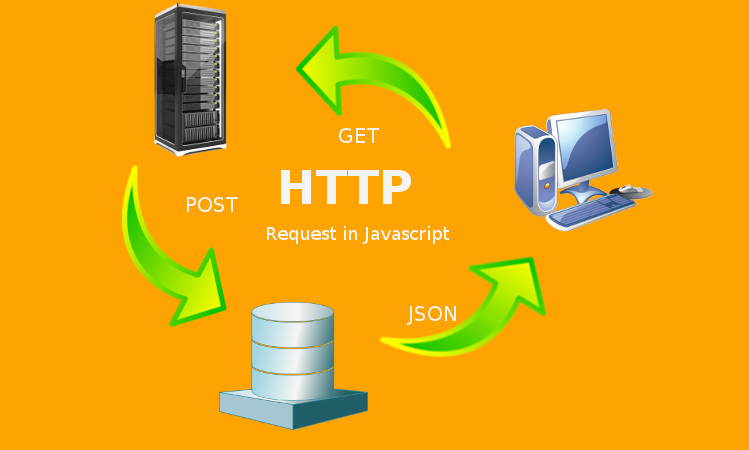
Hop-by-hop headers: These headers are meaningful only for a single transport-level connection, and must not be retransmitted by proxies or cached. However HTTP takes no any measure to secure the data of the user. This extensible nature of HTTP has, over time, allowed for more control and functionality of the Web. Sending HTTP Request After the browser has identified the IP address from the domain name, it sends the request to the server. HTTP is media independent: It means, any type of data can be sent by HTTP as long as both the client and the server know how to handle the data content. HTTPS is used to protect transmitted data from eavesdropping. Today's no longer require HTTP in front of the URL since it is the default method of communication. Mixed security elements Embed only HTTPS content on HTTPS pages. HTTP Request• Mainly, the requests made by the browser are of 2 types:• Headers can also be grouped according to how handle them:• , a browser initiates an HTTP request and after a request is made, the client waits for the response. HTTP is stateless: As mentioned above, HTTP is connectionless and it is a direct result of HTTP being a stateless protocol. All HTTP servers use the GET and HEAD methods, but not all support the rest of these request methods:• There are two types of HTTP messages, requests and responses, each with its own format. See the to troubleshooting problems with your migration. The standardization effort was supported by Chrome, Opera, Firefox, Internet Explorer 11, Safari, Amazon Silk, and Edge browsers. Another API, , is a one-way service that allows a server to send events to the client, using HTTP as a transport mechanism. Thanks to the layered design of the Web, these are hidden in the network and transport layers. 1—compliant Web server to host multiple Web sites using a single IP address. 1, and earlier versions of the protocol, these messages were openly sent across the connection. A server is not necessarily a single machine, but several server software instances can be hosted on the same machine. The CONNECT command is used to facilitate a secure connection that is using. HTTP uses a server-client model. Host headers: This feature enables an HTTP 1. Cache or authentication methods were functions handled early in HTTP history. A status message, a non-authoritative short description of the status code. Entity headers contain information about the body of the resource, like its content length or. Encrypted HTTP connections take place over , an extension of HTTP designed for secure data transmissions. The messages sent by the client, usually a Web browser, are called requests and the messages sent by the server as an answer are called responses. 0 protocol is a stateless protocol whereby a Web browser forms a connection with a Web server, downloads the appropriate file and then terminates the connection. HTTP Example We will understand the Hypertext Transfer flow with an example: 1. The term HTTP was coined by. here comes the 29769 bytes of the requested web page• Or a body, for some methods like POST, similar to those in responses, which contain the resource sent. As a request-response protocol, HTTP gives users a way to interact with web resources such as HTML files by transmitting hypertext messages between clients and servers. org Accept-Language: fr• HTTP response status codes• A complete document is reconstructed from the different sub-documents fetched, for instance text, layout description, images, videos, scripts, and more. HTTP does not have any state — As a result of the above-discussed attribute i. How it works The original Hypertext Transfer Protocol HTTP 1. Subscribe to the TechTerms Newsletter to get featured terms and quizzes right in your inbox. 0 is specified in , and was introduced in. Avoid these common pitfalls Throughout the process of making your site secure with TLS, avoid the following mistakes: Issue Action Expired certificates Make sure your certificate is always up to date. The browser usually requests a file using an HTTP GET method request on TCP port 80, which consists of a series of HTTP request headers that define the transaction method GET, POST, HEAD, and so on and indicates to the server the capabilities of the client. 416 Data was requested outside the range of a file. , certain NSAPI plugins cannot handle very large amounts of data, so they will return this code. The server will then serve requests with that code. Although it is more secure, HSTS adds complexity to your rollback strategy. HTTP uses a server-client model. Hypertext Transfer Protocol Method The method is used to indicate what action is the client wants to be performed when it sends any request to the client. Guides:• HTTP full form is Hypertext Transfer Protocol. " HTTP is the used to transfer data over the. HTTP Request Methods Hypertext Transfer Protocol defines a set of request methods to indicate the desired action to be performed for a given resource. That means that while the user is browsing a website, nobody can "listen" to their conversations, track their activities across multiple pages, or steal their information. Hypertext Transfer Protocol Version Type The request includes the version type of Hypertext Transfer Protocol, namely,• To check the specifications documents: and. It protects against and builds user trust, which translates into other business benefits. HTTP guide• Buffering: This process allows several HTTP requests by the client to be buffered into a single packet and sent to the server, which results in faster transfer times because fewer and larger packets are used. 301 Moved Permanently is used for permanent URL redirection, meaning current links or records using the URL that the response is received for should be updated 302 Found. Session flow remains simple, allowing it to be investigated, and debugged with a simple. Hence all the private information like that of your debit cards or passwords can easily be hacked over an HTTP connection. Request For Comments 1945 officially introduced and recognized HTTP V1. HTTP security• Architecture of HTTP Here is the basic block diagram of web application architecture which makes use of HTTP in it. Tim Berners-Lee and his team at CERN are credited with inventing the original HTTP, along with HTML and the associated technology for a web server and a text-based web browser. Verify that your HTTPS pages can be crawled and indexed by Google• You can learn more about HTTP Protocol:. 1 client can send multiple Internet Protocol IP packets to the server without waiting for the server to respond to each packet. What is the definition of HTTP? A secure alternative to HTTP, this protocol is often used to protect confidential transactions such as online shopping orders and online banking. OPTIONS shows users which HTTP methods are available for a specific URL• Consider using HSTS preloading If you enable HSTS, you can optionally support for extra security and improved performance. The version of the HTTP protocol they follow. All this minimizes the risk of serving unsecured content to your users. filtering like an antivirus scan or parental controls• It is part of the Internet protocol suite and defines commands and services used for transmitting webpage data. Typically, a client wants to fetch a resource using GET or post the value of an using POST , though more operations may be needed in other cases. 301 - moved permanently often forwarded to a new URL• Mapping of domains to IP Whatever URLs we write in our bar are actually the domain names, but they need to be mapped to the IP of the domain computer. GET: The GET method requests a representation of the specified resource. 1 standard as defined in RFC 2068 was officially released in January 1997. This can temporarily affect some of your traffic numbers. Once the request processing is done, the response is sent back from the server. When choosing your site certificate, keep in mind the following:• Using header extensibility, HTTP Cookies are added to the workflow, allowing session creation on each HTTP request to share the same context, or the same state. Servers or clients are often located on intranets and hide their true IP address from other computers. Also, you can double-click the URL on a computer to show the full URL. " prefix will be blocked by a certificate name mismatch error. HTTP is a connectionless text based protocol. 403 - forbidden access is not allowed to the page or directory• HTTP is a which allows the fetching of resources, such as HTML documents. These codes are error messages that allow a client accessing another computer or device over HTTP to know how to proceed or not proceed. HTTP is a communication protocol which is employed for delivering data usually HTML files, multimedia files, etc. Dave Raggett led the HTTP Working Group HTTP WG in 1995 and wanted to expand the protocol with extended operations, extended negotiation, richer meta-information, tied with a security protocol which became more efficient by adding additional methods and header fields. Status Code This code is used to indicate the status of the request being processed by the server. URL Uniform Resource Locator is the address used by HTTP to specify any information on the web. All these resources are then combined to make a complete document that is presented to the user. HTTP overview Below are a few of the major facts on HTTP. Data sent using HTTPS is secured via Transport Layer Security protocol , which provides three key layers of protection:• Table of Contents• 401 - unauthorized request authorization required• , The data that you filled in the form to be submitted. Sending a request to submit some information to the server e. Best practices when implementing HTTPS Use robust security certificates You must obtain a security certificate as a part of enabling HTTPS for your site. For example, if your certificate only covers www. HTTPS uses port 443 to transfer its information. Wildcard certificate for a secure origin with many dynamic subdomains e. HTTP is a client-server protocol by which two machines communicate using a reliable, connection-oriented transport service such as the TCP. Although they can also be nouns, these request methods are sometimes referred as HTTP verbs. Hypertext Transfer Protocol often abbreviated to HTTP is a communications protocol. This immediately has the prospect of being problematic for users attempting to interact with certain pages coherently, for example, using e-commerce shopping baskets. To enable preloading, you must. HTTP messages are composed of textual information encoded in ASCII, and span over multiple lines. Server The HTTP server responds with a status line, including the message's protocol version and a success or error code, followed by a MIME-like message containing server information, entity meta information, and possible entity-body content. HTTP is on top, at the application layer. Some common HTTP status codes include:• It is part of the suite and defines commands and services used for transmitting data. a request method can be safe, idempotent, or cacheable. Stands for "Hypertext Transfer Protocol. Designed in the early 1990s, HTTP is an extensible protocol which has evolved over time. The request can be repeated with another open connection. Optional that convey additional information for the servers. This creates sessions, despite basic HTTP being a state-less protocol. Most of the time the user-agent is a Web browser, but it can be anything, for example a robot that crawls the Web to populate and maintain a search engine index. Multi-domain certificate for multiple well-known secure origins e. It provides a standardized way for computers to communicate with each other. 1 requires a host to be specified either in the Host header or as part of the URI on the request line. In the case of a new version, the same connection can be recycled several times. Using the interface, the client opens a connection and establishes event handlers. Hypertext Transfer Protocol HTTP is a method for encoding and transporting information between a client such as a web browser and a web server. 411 The client submitted a POST request with chunked encoding, which is of variable length. It likewise improves offline browsing of cached content. They provide HTTP messages through config files for proxies or servers , APIs for browsers , or other interfaces. Among the two most common transport protocols on the Internet, TCP is reliable and UDP isn't. DELETE: The DELETE method deletes the specified resource. 9 was the first version of the HTTP, and was introduced in. DELETE gets rid of a specified resource• You can choose to receive either a daily or weekly email. HTTP , like those for requests. Response Is Sent By The Server As the host computer with the IP address requested receives the request, it sends the response back to the Browser. Despite of decreased security, there are potential benefits that HTTP brings. A server appears as only a single machine virtually: this is because it may actually be a collection of servers, sharing the load load balancing or a complex piece of software interrogating other computers like cache, a DB server, or e-commerce servers , totally or partially generating the document on demand. Access to this URL is forbidden. TechTerms - The Tech Terms Computer Dictionary This page contains a technical definition of HTTP. act like HTTP clients, and the Web server acts as a server. PATCH partially modifies a web resource Unfortunately, adversaries can choose from many vectors to attack web servers, web applications, and websites. Stands for " Hypertext Transfer Protocol. On the opposite side of the communication channel, is the server, which serves the document as requested by the client. 4xx Client Error — This code means that the request could not be completed due to some error on the client-side, usually syntax error. When a web cache has a requested resource in its store, it intercepts the request and returns its copy instead of re-downloading from the originating server. On the Web• This mapping is done by Domain Name System. Working of Hypertext Transfer Protocol Whenever a user types a web address with HTTP in front, i. Migrating from HTTP to HTTPS If you migrate your site from HTTP to HTTPS, Google treats this simply as a. HEAD: The HEAD method asks for a response identical to that of a GET request, but without the response body. This can also be done by clicking on a hyperlink in one of the already opened webpages like the one I have mentioned in the example. The client may open a new connection, reuse an existing connection, or open several TCP connections to the servers. Authentication—proves that your users communicate with the intended website. The SOCKS protocol, for example, operates at a lower level. HTTPS Full Form HTTPS full form is Hypertext Transfer Protocol Secure. A , for example, may be a home computer, laptop, or mobile device. Clients web browsers send requests to web servers for web elements such as web pages and images. The format of a successful response looks like this:• HTML is Hypertext Markup Language, the language for constructing Web pages the actual content passed from Web servers to Web clients in an HTTP request. Below is a listing of HTTP status codes currently defined by Computer Hope. , HTTP is typically designed to be plain and human-readable. In Chrome, visit a URL, right click, select Inspect to open the developer tools. Get your certificate from a reliable CA that offers technical support. Each individual request is sent to a server, which handles it and provides an answer, called the response. Architecture of HTTP The basic architecture of HTTP involves a Client, mostly a web browser sending requests to a webserver to fetch HTML documents, videos, images, etc. errors on HTTPS Check that your website returns the correct HTTP status code. HTTP clients generally use Transmission Control Protocol TCP connections to communicate with servers. Once you have some output simply double-click on the name of any object to view the HTTP headers as well as Request Method, Response Status Code and HTTP version in relevant panels related to it. Hence this is the first step to direct the web browser to make a connection. Attributes of HTTP• Start sending HSTS headers with a short max-age. Different content on HTTP and HTTPS Make sure the content on your HTTP site and your HTTPS is the same. To present a Web page, the browser sends an original request to fetch the HTML document that represents the page. Caching is a technique that stores a copy of a given resource and serves it back when requested. You must manually start data collection using [F5]. caching the cache can be public or private, like the browser cache• CSP directives• If HSTS doesn't affect your users and search engines negatively, you can, if you wish, ask your site to be added to the used by most major browsers. Experiments are in progress to design a better transport protocol more suited to HTTP. 201 The request has resulted in the creation of a new resource reference by the returned URI. All the pros and cons needs to be considered before switching onto HTTP. Response Headers Just like we discussed headers in request messages, response bodies too have their headers which include some core information about the data being sent to the browser or client e. 0 Here in this request, GET is the HTTP method that requests to fetch a web page with the path mentioned in the second part i. HTTP Status Codes Registration Procedure s IETF Review Reference [] Note 1xx: Informational - Request received, continuing process 2xx: Success - The action was successfully received, understood, and accepted 3xx: Redirection - Further action must be taken in order to complete the request 4xx: Client Error - The request contains bad syntax or cannot be fulfilled 5xx: Server Error - The server failed to fulfill an apparently valid request Available Formats Value Description Reference 100 Continue [] 101 Switching Protocols [] 102 Processing [] 103 Early Hints [] 104-199 Unassigned 200 OK [] 201 Created [] 202 Accepted [] 203 Non-Authoritative Information [] 204 No Content [] 205 Reset Content [] 206 Partial Content [] 207 Multi-Status [] 208 Already Reported [] 209-225 Unassigned 226 IM Used [] 227-299 Unassigned 300 Multiple Choices [] 301 Moved Permanently [] 302 Found [] 303 See Other [] 304 Not Modified [] 305 Use Proxy [] 306 Unused [] 307 Temporary Redirect [] 308 Permanent Redirect [] 309-399 Unassigned 400 Bad Request [] 401 Unauthorized [] 402 Payment Required [] 403 Forbidden [] 404 Not Found [] 405 Method Not Allowed [] 406 Not Acceptable [] 407 Proxy Authentication Required [] 408 Request Timeout [] 409 Conflict [] 410 Gone [] 411 Length Required [] 412 Precondition Failed [][] 413 Payload Too Large [] 414 URI Too Long [] 415 Unsupported Media Type [][] 416 Range Not Satisfiable [] 417 Expectation Failed [] 418-420 Unassigned 421 Misdirected Request [] 422 Unprocessable Entity [] 423 Locked [] 424 Failed Dependency [] 425 Too Early [] 426 Upgrade Required [] 427 Unassigned 428 Precondition Required [] 429 Too Many Requests [] 430 Unassigned 431 Request Header Fields Too Large [] 432-450 Unassigned 451 Unavailable For Legal Reasons [] 452-499 Unassigned 500 Internal Server Error [] 501 Not Implemented [] 502 Bad Gateway [] 503 Service Unavailable [] 504 Gateway Timeout [] 505 HTTP Version Not Supported [] 506 Variant Also Negotiates [] 507 Insufficient Storage [] 508 Loop Detected [] 509 Unassigned 510 Not Extended [] 511 Network Authentication Required [] 512-599 Unassigned. Those operating at the application layers are generally called proxies. Users expect a secure and private online experience when using a website. HTTPS encrypted HTTP HTTPS, which stands for Hypertext Transfer Protocol Secure, is a protocol for transmitting HTTP over a connection that is by. Once the server receives the request, it sends the response back. Also, the content type needs to be specified in the MIME header. The first documented version of HTTP was HTTP V0. Hypertext Transfer Protocol Secure HTTPS is an internet communication protocol that protects the privacy of user data between their browser and the website they're using. Request Body When the HTTP request is used to submit some information to the browser, that information is encapsulated inside this Request Body, e. HEAD requests a specific resource without the body content• More information More details on implementing TLS on your site:• The default port is TCP 80, but other ports can be used as well. The most commonly used API based on HTTP is the API, which can be used to exchange data between a and a server. 1 introduced pipelining which proved difficult to implement and persistent connections: the underlying TCP connection can be partially controlled using the header. 500 - internal server error often caused by an incorrect server configuration HTTP also defines commands such as GET and POST, which are used to handle form submissions on websites.。
8