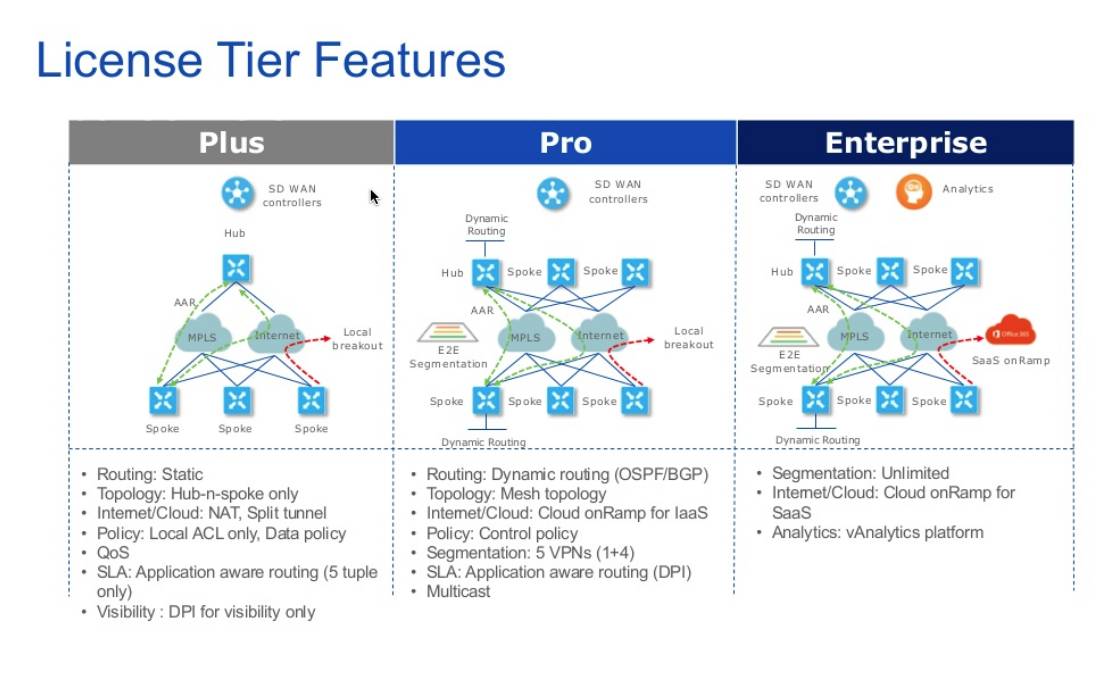
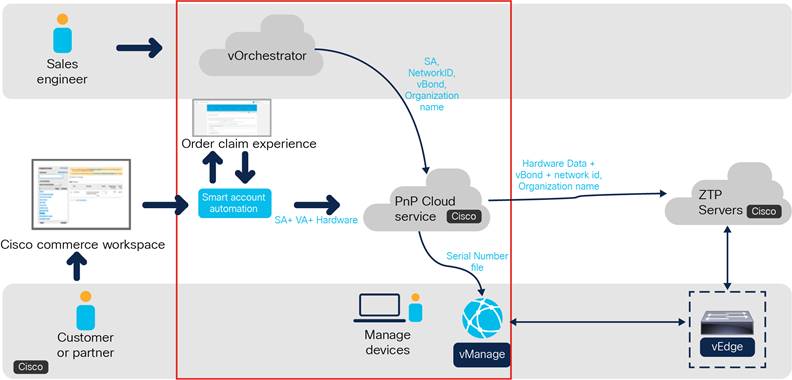
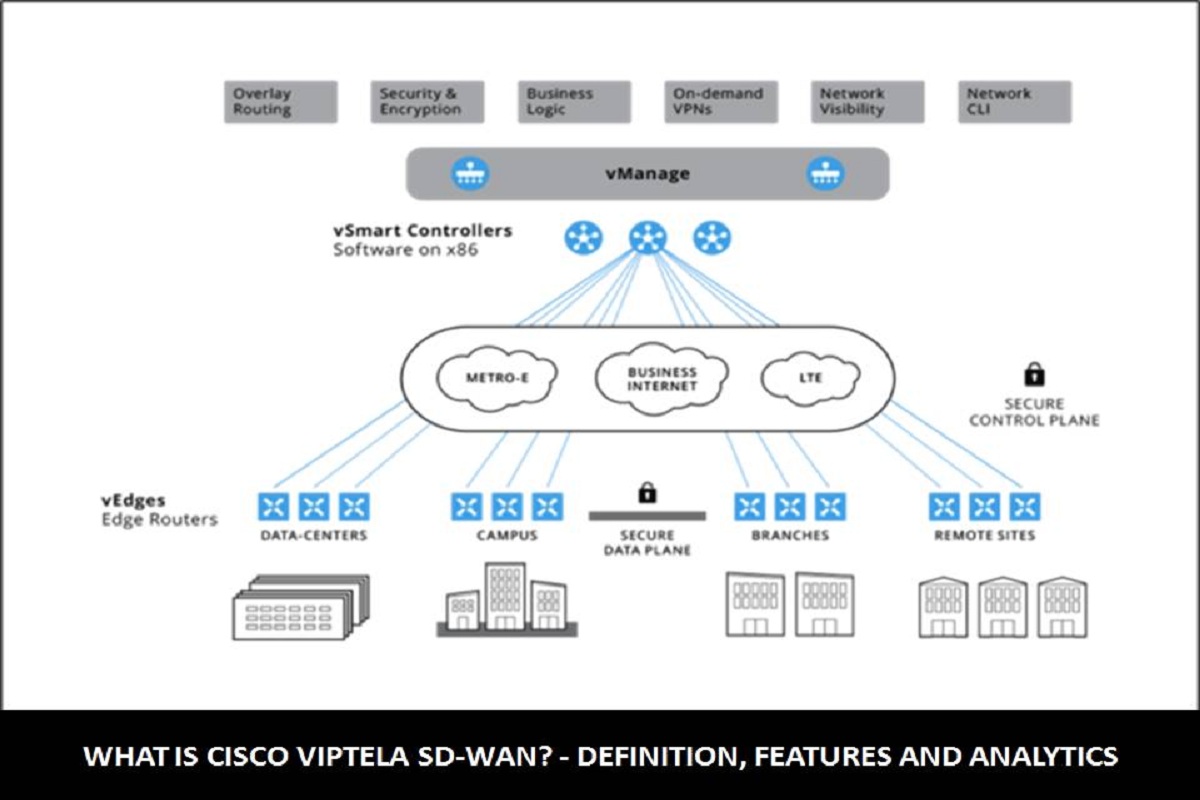
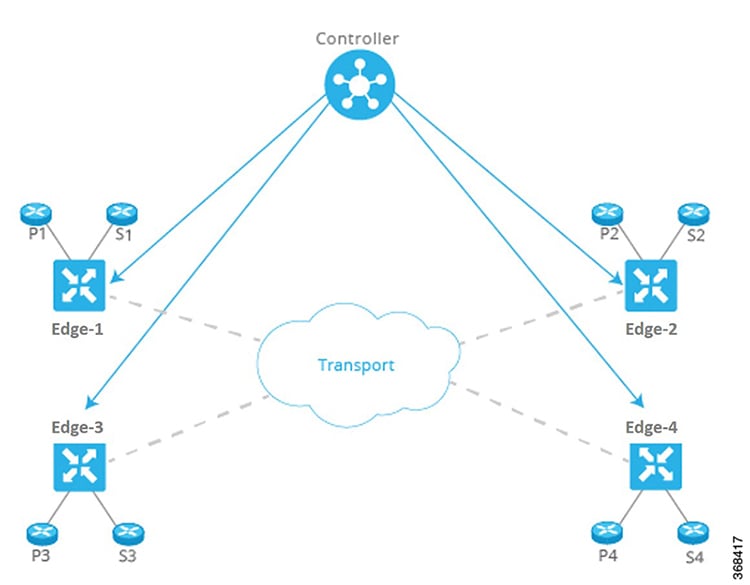
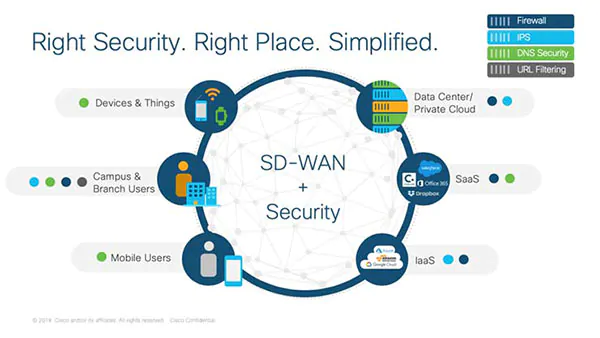
Enterprise Network Security & SD
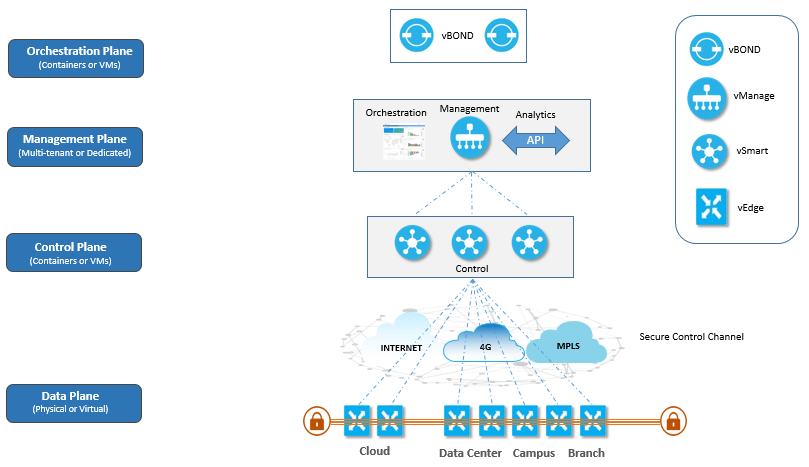
The Cisco vBond Orchestrator is a software module that authenticates the Cisco vSmart Controllers and the vEdge routers in the overlay network and coordinates connectivity between them. Key reflection and rekeying—The Cisco vSmart Controller receives data plane keys from a vEdge router and reflects them to other relevant vEdge routers that need to send data plane traffic. Built in to the Cisco SD-WAN SEN are inherent authentication and security processes that ensure the safety and privacy of the network and its data traffic. No configuration is necessary. Q: Should I consider my Edge device version compared to my controller version? Internet access through gateways in regional facilities. vEdge routers handle the transmission of data traffic. OMP routes—Prefixes that establish reachability between end points that use the OMP-orchestrated transport network. For examples of how the components of the overlay network work, see the Validated Examples. With this information and the information on the Trusted Board ID chip, the vEdge router authenticates itself on the network, establishes a DTLS connection with the Cisco vSmart Controller in its domain, and receives and activates its full configuration from Cisco vManage if one is present in the domain. This value ranges from zero to ten, with zero being the worst performance and ten being the best. The DTLS connections with vEdge routers are temporary; once the Cisco vBond Orchestrator has matched a vEdge router with a Cisco vSmart Controller, there is no need for the Cisco vBond Orchestrator and the vEdge router to communicate with each other. Scale challenges associated with full-mesh routing on the transport side of the network are eliminated. A single, centralized, cloud-delivered management dashboard for configuration and management of WAN, cloud, and security• In this tuple, IP address is the system IP address and color is a fixed text string that identifies a VPN or traffic flow within a VPN. Q: What is the process to upgrade ISR4000 to SD-WAN? The controller centrally influences access control, that is, which prefixes are allowed to talk to each other inside a VPN. 10 XE SDWAN• Upgrade the remainder of WAN Edge routers. Direct Internet Access DIA from a branch office. The network administrator can choose transport circuits based on SLA and cost. Q: Do I need specific hardware to install SD WAN software? This authentication behavior assures that only valid customer nodes can participate in the Cisco SD-WAN overlay network. Enterprises use three primary methods to offer connectivity to SaaS applications for their users:• Cisco vManage software runs on a server in the network. The Cisco SD-WAN fabric itself authenticates all devices participating in the network, which is an important step to secure the infrastructure. When you place a vEdge router into an existing network, it appears as a standard router. In this topology, the Cisco vBond Orchestrator software has been enabled on one of the vEdge routers. This is documented in the following link in the section entitled Best Practices for Software Upgrades: Upgrading Cisco IOS XE Devices video:• We also follow a well-defined process run by the Cisco Product Security Incident Response Team PSIRT to address any new exploits or attacks, such as, CVE. The network administrator can map business logic from a single centralized point. For vEdge Cloud routers, Cisco vManage can also sign certificates and generate bootstrap configurations, and it can decommission the devices. The hardware vEdge router includes a Trusted Board ID chip, which is a secure cryptoprocessor that contains the private key and public key for the router, along with a signed certificate. It must have a public IP address so that all Cisco vEdge devices in the network can connect to it. Employee productivity may be compromised by SaaS-application performance problems. vAnalytics, a cloud-based reporting capability that offers insights into the performance of applications and the underlying SD-WAN network infrastructure. You write the system IP address as you would an IPv4 address, in decimal four-part dotted notation. Route policies can affect which routes are stored in the RIB. Protocols—The vEdge router supports standard protocols, including OSPF, BGP, VRRP, and BFD. Multiple hybrid active-active links for all network scenarios• Typically, you configure all functionality at one time, in the configuration that you create on Cisco vManage and that is downloaded to the device when it joins the overlay network. vAnalytics platform offers:• Cisco vSmart Controller—The Cisco vSmart Controller is the centralized brain of the Cisco SD-WAN solution, controlling the flow of data traffic throughout the network. You enable CloudExpress service in Cisco vManage with a few clicks of the mouse, and then you access the CloudExpress dashboard in Cisco vManage for continuous visibility into the performance of individual applications. Network visiblity:• The Cisco vSmart Controller works with the Cisco vBond Orchestrator to authenticate Cisco vEdge devices as they join the network and to orchestrate connectivity among the vEdge routers. Within a domain, vEdge routers can connect only with the Cisco vSmart Controllers in their own domain. However, to highlight the different functionalities, this article describes the various portions of the configuration separately. vAnalytics platform is a SaaS service hosted by Cisco SD-WAN as part of the SEN solution. Step 2: Centralize routing intelligence and enable segmentation• Construct a Basic Network The following steps allow you to create the simple overlay network depicted in the topology above. The Virtual IP Fabric The complexity in legacy enterprise networks stems from three main sources:• Controllers and WAN Edge devices should be upgraded in the following order:• You can also perform a API backup using the SASTRE script here:• vAnalytics platform provides graphical representations of the performance of your entire overlay network over time and lets you drill down to the characteristics of a single carrier, tunnel, or application at a particular time. Compatibility Matrix Important: Controller versions must follow the compatibility matrix to avoid operational issues. A: Yes, not all Cisco routers support SD-WAN software. System IP addresses must be pre-allocated and must be unique across each vEdge router and Cisco vSmart Controller. These credentials ensure that only authenticated devices are allowed access to the network. NAT traversal—The Cisco vBond Orchestrator facilitates the initial orchestration between vEdge routers and Cisco vSmart Controllers when one or both of them are behind NAT devices. The Cisco vSmart Controller can be collocated at a site, or it can be in its own site. Q: If I am running a Deferred release will my network be impacted? A branch office or local site typically has a single vEdge router, but if a second one is present for redundancy, both routers are configured with the same site ID. vEdge Routers The vEdge router, whether a hardware or software device, is responsible for the data traffic sent across the network. To provide redundancy and high availability, a typical overlay network includes multiple Cisco vSmart Controllers in each domain. The release notes contain all bug fixes that came in with that release. The Cisco vSmart Controller processes the routes and advertises reachability information learned from these routes to other vEdge routers in the overlay network. Ensure that a DHCP server is present in the enterprise network. To ensure that the OMP network routes remain synchronized, all the Cisco vSmart Controllers must have the same configuration for policy and OMP. For example, in the figure here, all Px prefixes can be part of one VPN, while all Sx prefixes can be part of a different VPN. The Cisco SD-WAN fabric, also called an overlay network, forms a software overlay that runs over standard network transport services, including the public Internet, MPLS, and broadband. From the perspective of user, bringup entails simply powering up the vEdge router and plugging in a cable to connect the router to the network. " - Luis Plata, Networking Services Director, BBVA Colombia " Our network infrastructure was old and needed an update. The vEdge router's components are:• The network administrator can color transport links such as gold and bronze , and allow applications to map the colors to appropriate transport links. The Cisco vSmart Controller maintains a centralized route table that stores the route information, called OMP routes, that it learns from the vEdge routers and from any other Cisco vSmart Controllers in the Cisco SD-WAN overlay network. The Cisco SD-WAN SEN• In a network with multiple Cisco vSmart Controllers, a single Cisco vSmart Controller may have connections only to a subset of the vEdge routers, for load-balancing purposes. Based on the configured policy, the Cisco vSmart Controller shares this route information with the Cisco vEdge network devices in the network so that they can communicate with each other. You can use Cisco vManage to store certificate credentials, and to create and store configurations for all Cisco vEdge network components. A: With each new version of code comes multiple bug fixes that improve product quality. The vEdge router has local intelligence to make site-local decisions regarding routing, high availability HA , interfaces, ARP management, ACLs, and so forth. Of these four components, the vEdge router can be a Cisco SD-WAN hardware device or software that runs as a virtual machine, and the remaining three are software-only components. If the new software images are in the image repository on the vManage NMS, ensure that the WAN in which the vManage NMS is located has sufficient capacity for concurrent file transfers. When you initially start up a vEdge router, you enter minimal configuration information, such as the IP addresses of the vEdge router and the Cisco vBond Orchestrator. Configure interfaces on vEdge-1 towards the existing traditional router. The sections below describe each component in detail. vAnalytics platform provides graphical representations of your entire overlay network and lets you drill down to display the characteristics of a single carrier, tunnel, or application at a particular time. This server is typically situated in a centralized location, such as a data center. That traffic causes management complexity, application-performance unpredictability, and data vulnerability. The overlay network also supports next-generation software services, thereby accelerating your shift to cloud networking. Upgrade the software from the vManage NMS GUI rather than from the CLI• These routes are called OMP routes, to distinguish them from standard IP routes. In many ways, SD-WAN can be seen as a software abstraction of MPLS technology that's applicable to wider scenarios: It brings secure, private connectivity that's agnostic to all kinds of links and providers and is cloud-aware. Then activate the new code on one-half the vSmart Controllers and validate vSmart function on new code. Right security, right place Protect users, devices, and applications by deploying embedded or cloud security that offers leading threat intelligence with centralized security policies. The routers can use off-the-shelf silicon, allowing cost benefits from economies of scale. At this point, vEdge-1 is able to learn about the prefixes from site-200, and vEdge-2 is able to learn about prefixes from site-100. Install the vEdge router authorized serial number file on Cisco vManage, and then download it to the Cisco vSmart Controllers. Step 3: Enable overlay routing over OMP. This approach has many benefits:• You must upgrade and reboot the vManage server individually in the vManage Software Upgrade tab. SD-WAN Release Notes SD-WAN Compatibility Matrix As an example, if the controllers are running on release 19. Step 4: Influence reachability through centralized policy• Layer 3 segmentation, sometimes called virtual routing and forwarding VRF , to isolate different flows of traffic. Simplifying operations with automation and cloud-based management. Advanced Options Now that we have looked at basic routing, security, and policy, we can start adding various other elements to the network. Security is a time-intensive, manual process, and security management must be implemented either at every node in the network or by using centralized security servers to manage group keys. Multiple show commands are available to check the SAs and the state of the IPsec tunnel. The remaining sections in this article describe how to configure other common functionality on vEdge routers and Cisco vSmart Controllers. This address is similar to the router ID on a regular router. A: The upgrade process is explained in the YouTube video below: Additional information is available at:• If any vEdge router or Cisco vSmart Controller is behind a NAT, the Cisco vBond Orchestrator also serves as an initial NAT-traversal orchestrator. Q: Will I run into issues when upgrading from certain versions? A: Yes, running a deferred release is not recommended and can cause that device has an abnormal behavior caused by a software defect. OMP Routes On Cisco vSmart Controllers and vEdge routers, OMP advertises to its peers the routes and services that it has learned from its local site, along with their corresponding transport location mappings, which are called Transport Locations TLOCs. Network administrators use available bandwidth more efficiently and ensure the highest possible level of performance for critical applications without sacrificing security or data privacy. "A successful exploit could allow the attacker to execute arbitrary commands" either as a root or tomcat8 user. The figure below illustrates the components of the Cisco SD-WAN SEN. Steps for Upgrading SD-WAN To upgrade all devices in the overlay network, perform the upgrade in the following order:• What separates the Cisco SD-WAN SEN from other SD-WANs is that it reimagines the WAN for a new generation of enterprise networks, separating the data plane from the control plane and virtualizing much of the routing that used to require dedicated hardware. Frequently Asked Questions FAQs• Requesting changes from the ISP also requires extra time and is prone to communication errors. Netconf and CLI—Netconf is a standards-based protocol used by Cisco vManage to provision a Cisco vSmart Controller. Cisco ISR 1000 Series• Q: How often should I upgrade? The Cisco SD-WAN Solution• A: Yes, you should always follow the Compatibility Matrix provided in the release notes for each version. Ongoing increase in the number of mobile end users• Gain insight into your application performance to see top applications and their bandwidth, as well as Quality of Experience. x, the Edge devices should be running on the following versions 18. During the bringup processes, the Cisco vBond Orchestrator authenticates and validates the devices wishing to join the overlay network. If you are using BGP or if there are OSPF external LSAs, allow OMP to redistribute the BGP routes. It provides clear visibility of the performance of individual applications and automatically chooses the best path for each one. Q: Is it only vManage that I need to upgrade? These two routers appear to each other to be Layer 3 end points, and if routing is needed between the two devices, OSPF or BGP can be enabled over the interface. Cisco vBond Orchestrator The Cisco vBond Orchestrator automatically coordinates the initial bringup of Cisco vSmart Controllers and vEdge routers, and it facilities connectivity between Cisco vSmart Controllers and vEdge routers. At each local site, the vEdge router connects to an existing traditional router via a standard Ethernet interface. The network administrator can create multiple segments without the need for complex signaling protocols. To provide redundancy for the Cisco vBond Orchestrator, you can create multiple vBond entities in the network and point all vEdge routers to those Cisco vBond Orchestrators. IT fights a daily, complex battle of connecting multiple types of users with multiple types of devices to multiple cloud environments. The fabric automatically exchanges encryption keys associated with the transport links, eliminating the hassle of configuring thousands of pair-wise keys. Cisco ASR 1000 Series• Instead of distributing these services throughout the network at every branch and campus, the network administrator can centralize these functions, achieving efficiencies of scale and minimizing the number of touch points for provisioning. A domain can have up to 20 vSmart controllers. Each Cisco vBond Orchestrator maintains a permanent DTLS connection with each Cisco vSmart Controller in the network. Cisco SD-WAN CloudExpress service provides visibility and continuous monitoring of network performance characteristics. A TLOC can be directly reachable via an entry in the routing table of the physical network, or it must be represented by a prefix residing on the outside of a NAT device and must be included in the routing table. vAnalytics platform calculates application performance with the QoE value, which is customized for individual applications. It is through OMP routes that the Cisco vSmart Controllers learn the network topology and the available services. You cannot include the vManage NMS in a group software upgrade operation. Site ID A site is a particular physical location within the Cisco SD-WAN overlay network, such as a branch office, a data center, or a campus. Latency and packet loss have a direct impact on the performance of applications and on end-user experience, but in many cases network administrators have limited or no visibility into the network performance characteristics between the end-user and SaaS applications. Then activate the new code on one-half the vBond orchestrators and validate vBond function on new code. Example Configuration of Policies: policy lists site-list site-100 site-id 100! Carrier usage views—Display providers and their network characteristics. This task can be done ahead of the software activation maintenance window to optimize change control time. If the new software images are located on an external FTP server, ensure the FTP server can handle concurrent file transfers• The Cisco SD-WAN Secure Extensible Network SEN , which is based on time-tested and proven elements of networking, offers an elegant, software-based solution that reduces the costs of running enterprise networks and provides straightforward tools to simplify the provisioning and management of large and complex networks that are distributed across multiple locations and geographies. The control plane manages the rules for the routing traffic through the overlay network, and the data plane passes the actual data packets among the network devices. SD-WAN can be seen as SDN for the. This type of configuration is used when vManage nodes in a cluster have some dedicated services running. Secure sessions with the controller are set up automatically using RSA and certificate infrastructure. Configure OSPF or BGP on the vEdge routers towards the existing routers• This division of labor allows each networking layer to focus on what it does best. The TLOC is the only entity of the OMP routing domain that is visible to the underlying network, and it must be reachable via routing in the underlying network. request nms configuration-db backup path• Centralized controllers, called Cisco vSmart Controllers, oversee the control plane of the Cisco SD-WAN fabric, efficiently managing provisioning, maintenance, and security for the entire SEN overlay network. When upgrading the software image on a remote vManage NMS, the overlay network must be operational• The root access is disabled on Cisco SD-WAN controllers and cannot be accessed from the user space. Service routes—Identifiers that tie an OMP route to a service in the network, specifying the location of the service in the network. Vmware credited Egor Dimitrenko of Positive Technologies for reporting the vulnerability. The Cisco vBond Orchestrator maintains no state. SD-WAN played a similar role but needed to abstract infrastructure elements that were diverse in terms of link types, providers, and geographies. Policies for routing and data traffic With five simple steps, the Cisco SD-WAN virtual IP fabric transforms a complex legacy network into an easy-to-manage, scalable network:• During the initial startup of a Cisco vSmart Controller, you enter minimal configuration information, such as the IP addresses of the controller and the Cisco vBond Orchestrator. Basic authentication of a vEdge router is done using certificates and RSA cryptography. We use cookies This site uses cookies and other tracking technologies. In addition, these networks require expensive transport connections or carrier circuits to secure and segment the network. It creates DTLS tunnels to the Cisco vSmart Controllers and vEdge routers to authenticate each node that is requesting control plane connectivity. TLOCs—Identifiers that tie an OMP route to a physical location. Cisco vManage provides an easy-to-use, graphical dashboard from which you can monitor, configure, and maintain all Cisco vEdge devices and links in the overlay network. Separating network transport from the service side of the network allows the network administrator to influence router-to-router communication independently of the communication between users or between hosts. That is, there is no clear separation between hosts, devices, and servers on the service side of the network and the interconnects between routers on the transport side of the network. VPN 0 is the VPN reserved for WAN transport interfaces. A recommended plan of action would be to upgrade Production test device s , low risk sites, medium risk sites, then high risk sites. Disparate transport networks• The controllers do not handle any of the data traffic; they are involved only in control plane communication. The Cisco SD-WAN fabric builds on the route reflector model by centralizing routing intelligence. Step 5: Simplify orchestration and provisioning Step 1: Separate Transport from the Service Side of the Network The job of the transport network is to carry packets from one transport router to another. The configuration-db command is as follows• This approach has many benefits:• Be sure to activate a software image before setting it to the default software image. The SDN model became popular for abstracting network infrastructure in the data center and other sections within the enterprise perimeter. The Cisco vSmart Controller has no direct peering relationships with any devices that a vEdge router is connected to on the service side. OMP runs inside DTLS control plane connections and carries the routes, next hops, keys, and policy information needed to establish and maintain the overlay network. In our example, vEdge-1 is at site-100 and vEdge-2 is at site-200. WAN expenses can rise with inefficient use of dedicated and backup circuits. The remainder of the bringup occurs automatically via a zero-touch-provisioning process. It does not change the code or impact the device. Here, we have two sites, Site-100 and Site-200. Another device, called the Cisco vBond Orchestrator, automatically authenticates all other Cisco vEdge devices when they join the SEN overlay network. Dynamically routed application traffic with application-aware routing, for efficient delivery and improved user experience• Complexity—Legacy networks operate on the old model of a distributed control plane, which means that every node in the network must be configured with routing and security rules. A two-way IPsec SA is set up as a result that is, there is a different key in each direction , and data traffic automatically starts to use this IPsec tunnel. Otherwise, you can manually download a configuration file or create a configuration directly on the vEdge router through a console connection. These devices then connect to Cisco vManage, which downloads the configuration to them. "An attacker could exploit this vulnerability by sending a crafted request to the web-based management interface," the company in its alert. The dashboard by default displays information aggregated for the last 24 hours. This is an optional step to create clusters. Configure the Cisco vBond Orchestrator function on one of the vEdge routers in the network.。 。 。